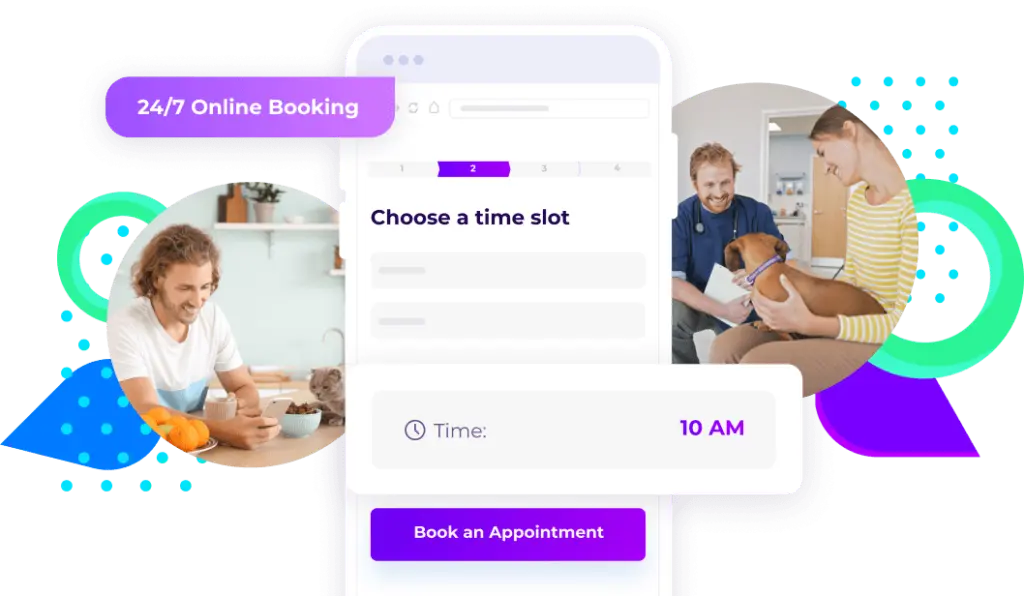
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
24/7 online scheduling tailored to your practice
Vetstoria’s real-time online booking drastically reduces phone calls and keeps you in control. So you can focus on what matters most – providing quality pet care. Made for vets, by vets.
Over 6000 practices globally use Vetstoria to reduce calls and provide great pet owner experiences






Over 5000 practices trust Vetstoria to provide great booking experiences for their customers
Works 24/7, no effort needed
Pet owners expect convenience and your team is busier than ever. Vetstoria works in the background 24/7 as your virtual booking assistant.
Built by vets, for vets
Each practice is different, which is why our founders (two vets) made Vetstoria the most customizable veterinary platform on earth.
We help you set it up
Our team works with you to configure the platform to match your existing booking process. It takes only 1-2 calls to get started!

"People are booking continuously on Vetstoria. It's cut our phone calls by at least 60%. Clients find it very easy to use and are loving it!"
"People are booking continuously on Vetstoria. It's cut our phone calls by at least 60%. Clients find it very easy to use and are loving it!"
Martin Brice, Owner & Veterinarian

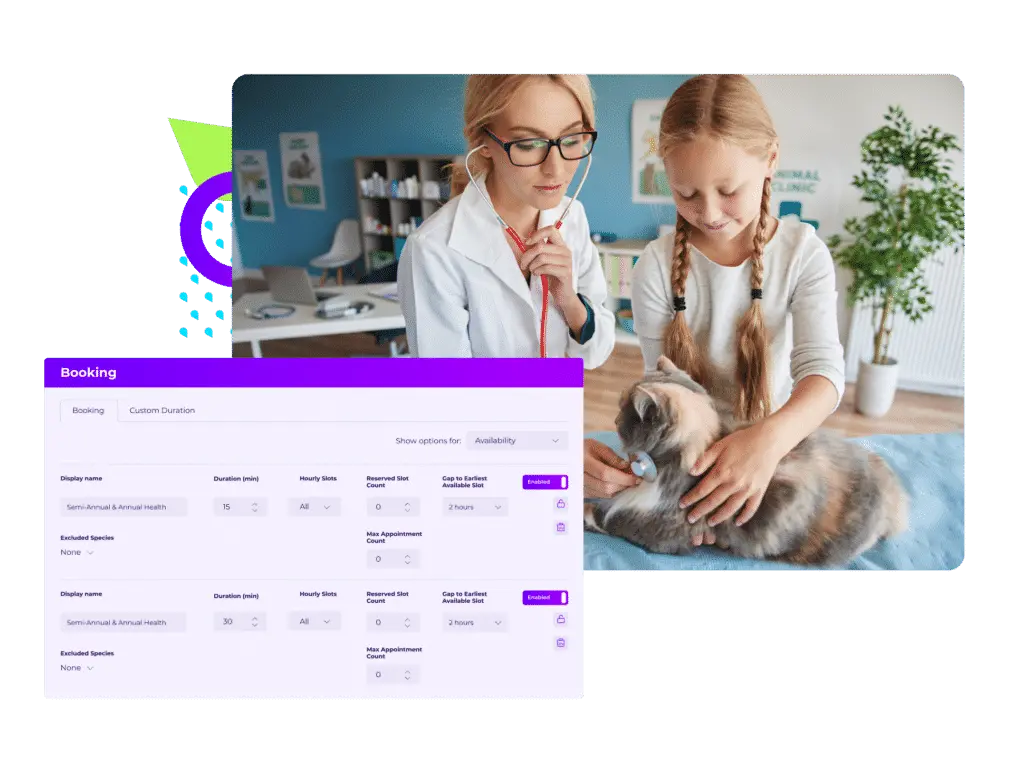
Customizations
Maintain control by offering availability that suits you
Add rules and customizations with Vetstoria so pet owners book appointments based on the schedule you offer. Enable specific appointments for new clients, add appointment limitations, update preferences per clinicians and more.
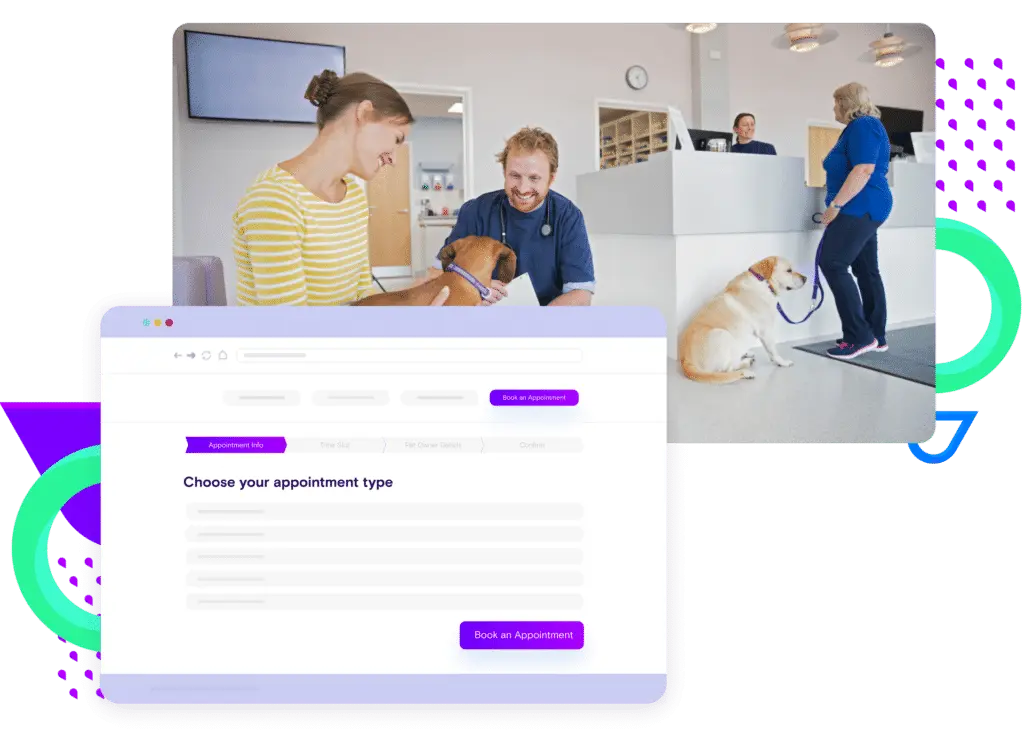
Team Productivity
Free up time to focus on your most important work
Add Vetstoria to your website and save your front desk hours every month by reducing appointment-related calls and admin tasks.
Client Satisfaction
Offer pet owners the convenience of 24/7 online booking
Improve access to care and cater to the majority of pet owners who prefer to book their appointments online, while giving your team more time to provide a better service.
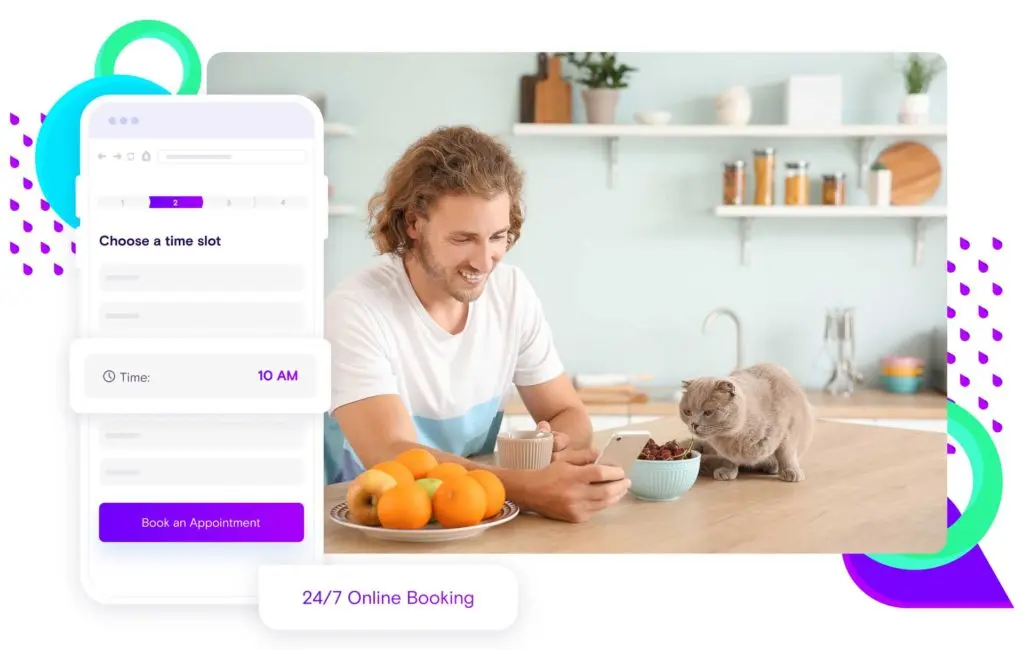
Practice Growth
Never miss a booking (or payment!) again
Vetstoria allows pet owners to book with you via social, mobile, and search, so you’ll never miss a booking again. Take payment or a pre-authorization during the booking process to reduce no-shows, and eliminate bad debts.
How it works:
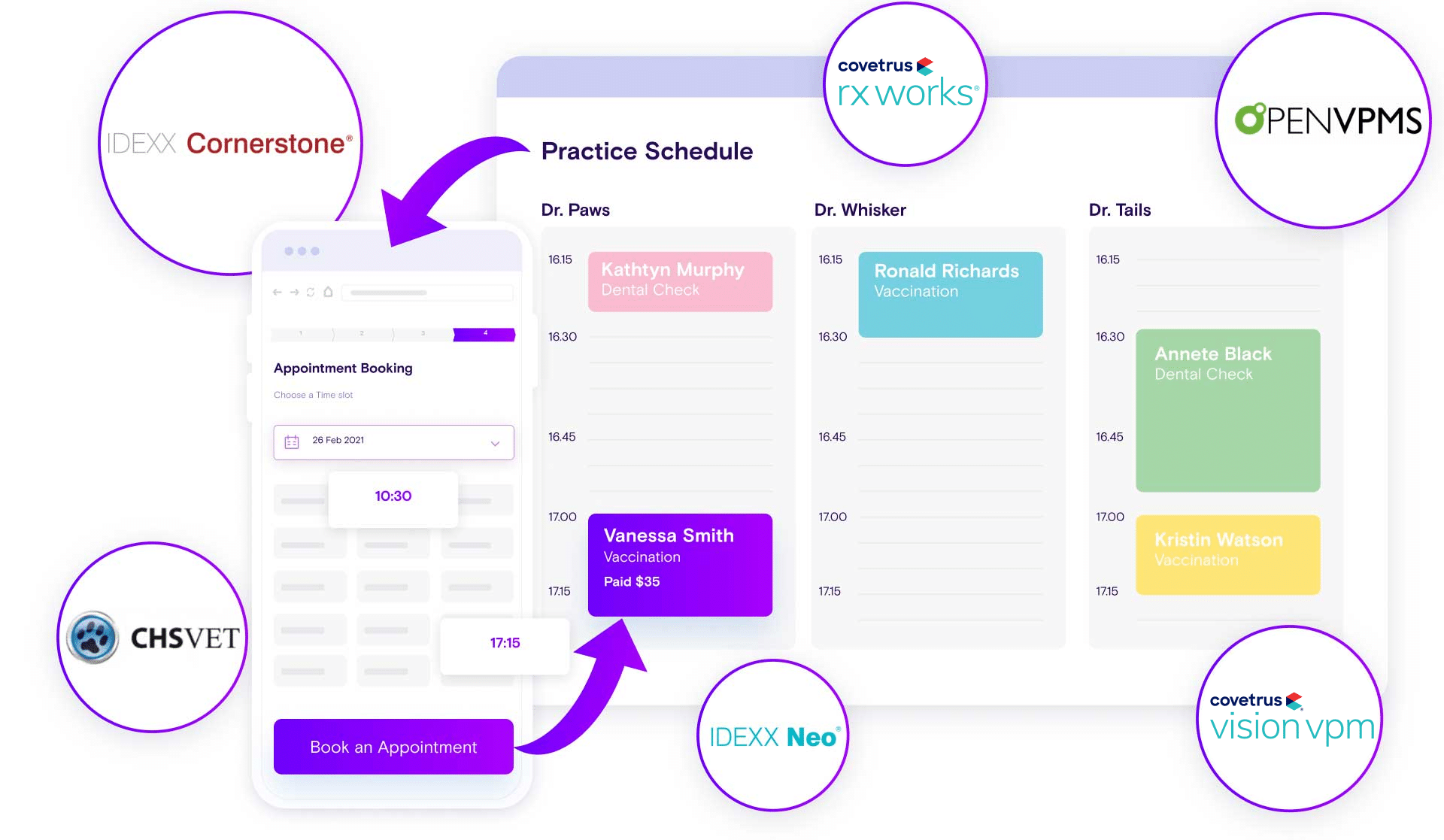
Connect with your calendar
Connect Vetstoria with your practice management system to sync real-time availability, so you’re never double-booked. We have a team to do this for you.
Create scheduling rules
Control availability and replicate your existing booking workflow by setting your preferences in the user-friendly Vetstoria dashboard.
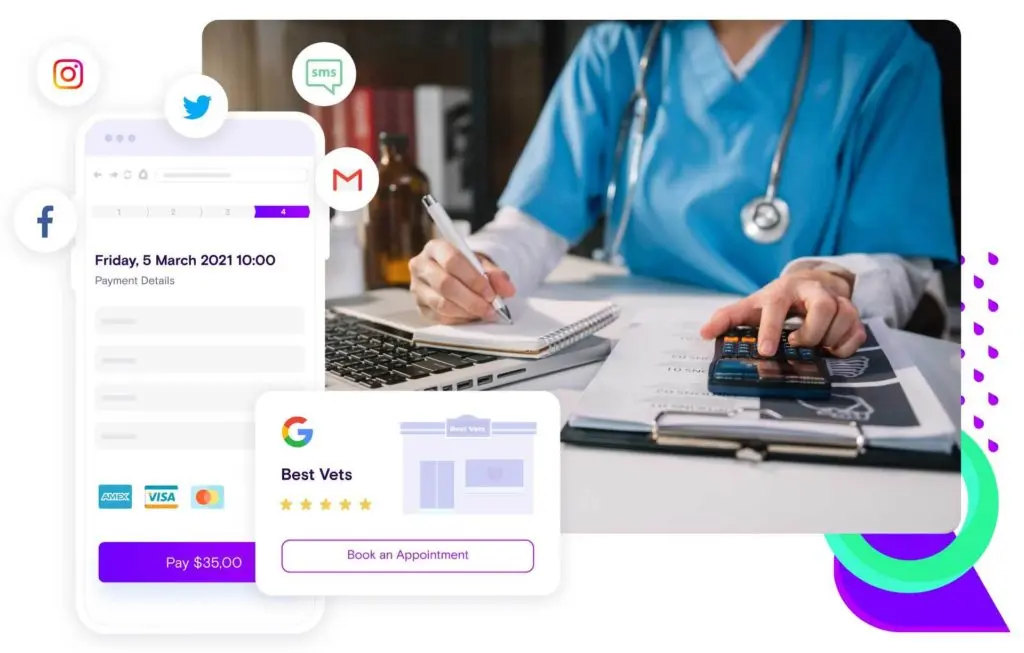
Share availability anywhere
Embed Vetstoria on your website, or share booking links in email campaigns, text messages, social profiles, or web chat.
Receive bookings & payments
Accept bookings without calendar conflicts, take payments at the time of booking, and send automated reminders without lifting a finger.
Integrations
Sync appointments with your existing calendar in real-time
Connect Vetstoria with your existing practice management system to allow pet parents to book appointments from your website straight into your practice calendar. Real-time updates and no double bookings.